Integrating Fiberlink MaaS360 with Cisco Identity Services Engine
22
MDM Profiles
Device profiles are an important concept of mobile device management. They are defined as part of the
MDM protocol implemented by the operating system. The concept can be extended to application
profiles, but as discussed here, they are found under the settings of the device. Each profile can contain
one or more payloads. A payload has all the attributes needed to provision some aspect of built-in system
functions, such as PIN lock and Device Restrictions. Android and Apple differ in what payloads are
supported. One special payload will be an MDM payload that defines the MDM server as the device
administrator. There can only be one MDM payload installed on any device. The profile containing the
MDM payload may not be locked and the user is free to delete it at any time. When this occurs, all other
profiles installed by the MDM are also removed, essentially resulting in a corporate wipe.
The MDM may lock any profile that it installed to prevent the user from removing them individually.
The MDM is allowed to inspect other profiles, such as the Wi-Fi profile installed by ISE, but is not
allowed to remove any profile that it did not install. Since multiple profiles can be installed on a device
and profiles have payloads, it is possible to have a payload collision. Devices with multiple security
payloads will install all the payloads by aggregating the most secure settings from each. In most other
cases the first payload is installed and subsequent payloads are ignored or multiple payloads are
accepted. For example, the device can have multiple VPNs provisioned, but only one can be named XYZ.
MDM profiles can be applied to devices associated to users that belong to a user group. Configuring this
with Fiberlink MaaS360, administrator will take following steps:
1. Configure Fiberlink MaaS360 Cloud Extender to import groups from Corporate Directory.
2. Create profiles as desired for different AD Group Types.
3. Bind Profiles to AD groups.
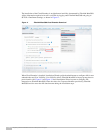
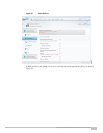
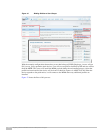
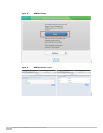
Figure 15 shows the creation of a profile.
On Fiberlink MaaS360 Administration Portal, Go to Security > Policy > Add Policy to create policies.