Unied Access Point Administrator’s Guide
Unied Access Point Administrator’s Guide
Page 15
March 2012
Section 2 - Getting Started
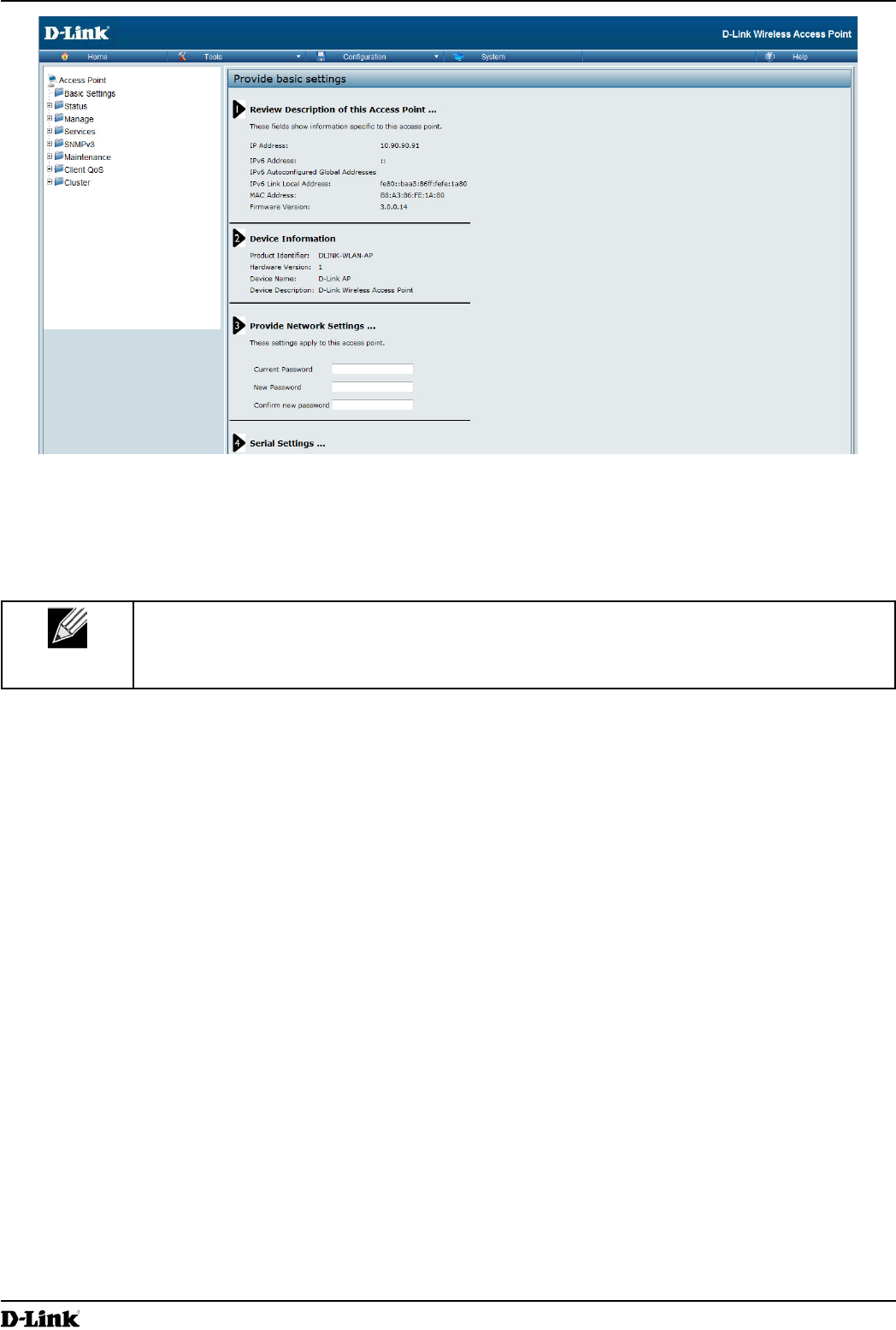
Figure 3 - Provide Basic Settings
5.) Verify the settings on the Basic Settings page.
•) Review access point description and provide a new administrator password for the access point if you do not
want to use the default password, which is admin.
•) Click the Apply button to activate the wireless network with these new settings.
Note: The changes you make are not saved or applied until you click Apply. Changing some
access point settings might cause the AP to stop and restart system processes. If this happens,
wireless clients will temporarily lose connectivity. We recommend that you change access point
settings when WLAN trafc is low.
For information about the elds and conguration options on the Basic Settings page, see “Basic Settings” on
page 16.
6.) If you do not have a DHCP server on the management network and do not plan to use one, you must change
the Connection Type from DHCP to Static IP.
You can either assign a new Static IP address to the AP or continue using the default address. We recommend
assigning a new Static IP address so that if you bring up another UAP on the same network, the IP address
for each AP will be unique. To change the connection type and assign a static IP address, see “Conguring the
Ethernet Settings” on page 18 (CLI) or “Ethernet Settings” on page 35 (Web).
7.) If your network uses VLANs, you might need to congure the management VLAN ID or untagged VLAN ID on
the UAP in order for it to work with your network.
For information about how to congure VLAN information, see “Conguring the Ethernet Settings” on page 18
(CLI) or “Ethernet Settings” on page 35 (Web).
8.) If your network uses IEEE 802.1X port security for network access control, you must congure the 802.1X
supplicant information on the AP.
For information about how to congure the 802.1X user name and password, see “Conguring IEEE 802.1X
Authentication” on page 19.


















