Unied Access Point Administrator’s Guide
Unied Access Point Administrator’s Guide
Page 85
March 2012
Section 7 - Maintaining the Access Point
Upon activation, the packet capture proceeds until one of the following occurs:
•) The capture time reaches congured duration.
•) The capture le reaches its maximum size.
•) The administrator stops the capture.
During the capture, you can monitor the capture status, elapsed capture time, and the current capture le size. This
information can be updated, while the capture is in progress, by clicking Refresh.
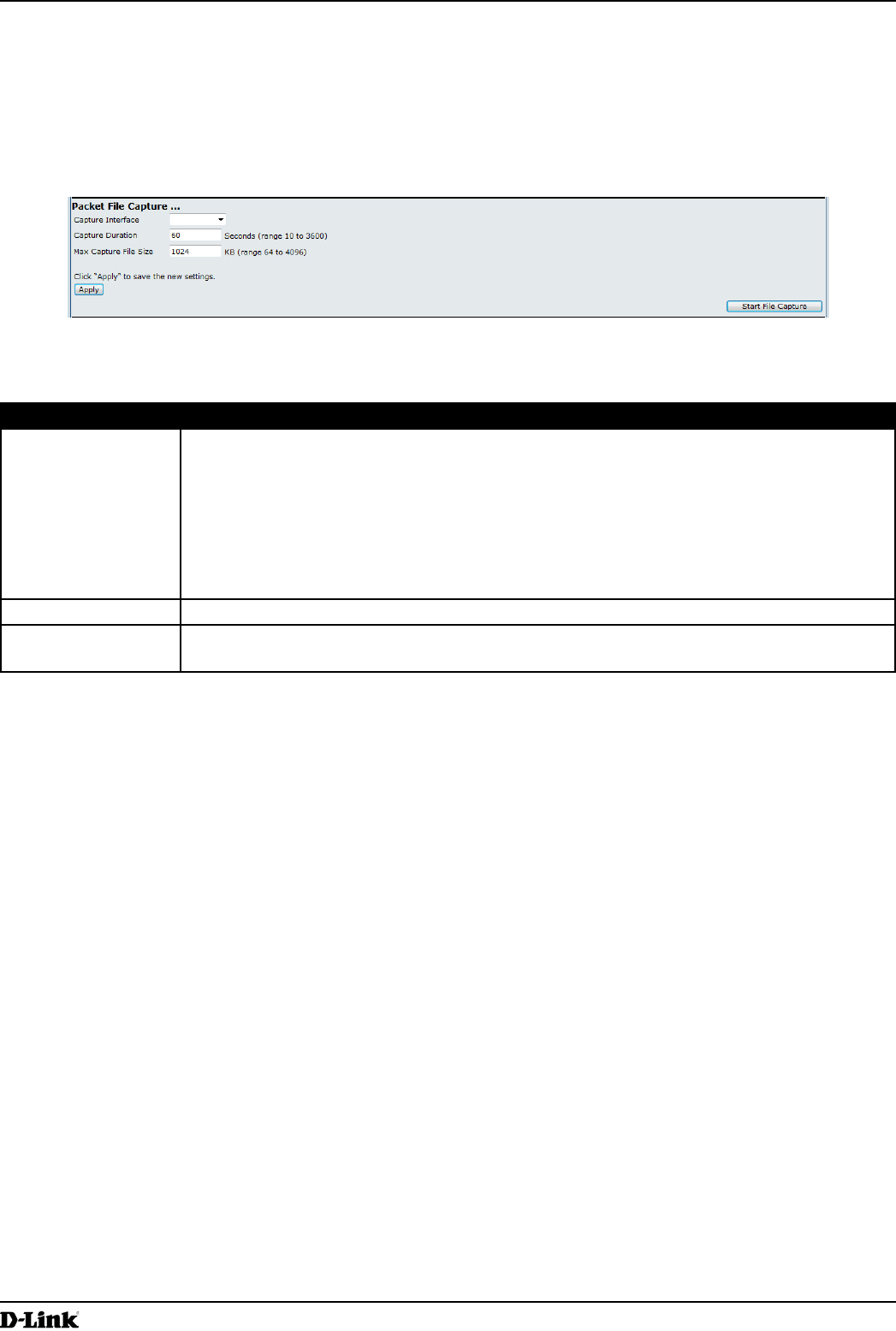
Figure 55 - Packet File Capture
The following table describes the elds to congure the packet capture status.
Field Description
Capture Interface Select an AP Capture Interface name from the drop-down menu. AP capture interface
names are eligible for packet capture are:
•) brtrunk - Linux bridge interface in the AP
•) eth0 - 802.3 trafc on the Ethernet port.
•) wlan0 - VAP0 trafc on radio 1.
•) wlan1 - VAP0 trafc on radio 2.
•) radio1 - 802.11 trafc on radio 1.
•) radio2 - 802.11 trafc on radio 2.
Capture Duration Specify the time duration in seconds for the capture (range 10 to 3600).
Max Capture File
Size
Specify the maximum allowed size for the capture le in KB (range 64 to 4096).
Table 49 - Packet File Capture
Remote Packet Capture
Remote Packet Capture allows you to specify a remote port as the destination for packet captures. This feature works
in conjunction with the Wireshark network analyzer tool for Windows. A packet capture server runs on the AP and
sends the captured packets via a TCP connection to the Wireshark tool.
A Windows PC running the Wireshark tool allows you to display, log, and analyze captured trafc.
When the remote capture mode is in use, the AP doesn’t store any captured data locally in its le system.
Your can trace up to ve interfaces on the AP at the same time. However, you must start a separate Wireshark session
for each interface. You can congure the IP port number used for connecting Wireshark to the AP. The default port
number is 2002. The system uses 5 consecutive port numbers starting with the congured port for the packet capture
sessions.
If a rewall is installed between the Wireshark PC and the AP, these ports must be allowed to pass through the
rewall. The rewall must also be congured to allow the Wireshark PC to initiate TCP connection to the AP.
To congure Wireshark to use the AP as the source for captured packets, you must specify the remote interface in the
“Capture Options” menu. For example to capture packets on an AP with IP address 192.168.1.10 on radio 1 using the
default IP port, specify the following interface:
rpcap://192.168.1.10/radio1


















