Unied Access Point Administrator’s Guide
Unied Access Point Administrator’s Guide
Page 86
March 2012
Section 7 - Maintaining the Access Point
To capture packets on the Ethernet interface of the AP and VAP0 on radio 1 using IP port 58000, start two Wireshark
sessions and specify the following interfaces:
rpcap://192.168.1.10:58000/eth0
rpcap://192.168.1.10:58000/wlan0
When you are capturing trafc on the radio interface, you can disable beacon capture, but other 802.11 control frames
are still sent to Wireshark. You can set up a display lter to show only:
•) Data frames in the trace.
•) Trafc on specic BSSIDs.
•) Trafc between two clients.
Some examples of useful display lters are:
•) Exclude beacons and ACK/RTS/CTS frames:
!(wlan.fc.type_subtype == 8 || wlan.fc.type == 1)
•) Data frames only:
wlan.fc.type == 2
•) Trafc on a specic BSSID:
wlan.bssid == 00:02:bc:00:17:d0
•) All trafc to and from a specic client:
wlan.addr == 00:00:e8:4e:5f:8e
In remote capture mode, trafc is sent to the PC running Wireshark via one of the network interfaces. Depending on
where the Wireshark tool is located the trafc can be sent on an Ethernet interface or one of the radios. In order to
avoid a trafc ood caused by tracing the trace packets, the AP automatically installs a capture lter to lter out all
packets destined to the Wireshark application. For example if the Wireshark IP port is congured to be 58000 then the
following capture lter is automatically installed on the AP:
not portrange 58000-58004.
Enabling the packet capture feature impacts performance of the AP and can create a security issue (unauthorized
clients may be able to connect to the AP and trace user data). The AP performance is negatively impacted even if
there is no active Wireshark session with the AP. The performance is negatively impacted to a greater extent when
packet capture is in progress.
Due to performance and security issues, the packet capture mode is not saved in NVRAM on the AP; if the AP resets,
the capture mode is disabled and the you must re-enable it in order to resume capturing trafc. Packet capture
parameters (other than mode) are saved in NVRAM.
In order to minimize performance impact on the AP while trafc capture is in progress, you should install capture lters
to limit which trafc is sent to the Wireshark tool. When capturing 802.11 trafc, large portion of the captured frames
tend to be beacons (typically sent every 100ms by all Access Points). Although Wireshark supports a display lter for
beacon frames, it does not support a capture lter to prevent the AP from forwarding captured beacon packets to the
Wireshark tool. In order to reduce performance impact of capturing the 802.11 beacons, you can disable the capture
beacons mode.
The remote packet capture facility is a standard feature of the Wireshark tool for Windows.
Note: Remote packet capture is not standard on the Linux version of Wireshark; the Linux version
doesn’t work with the AP.
Wireshark is an open source tool and is available for free; it can be downloaded from http://www.wireshark.org.
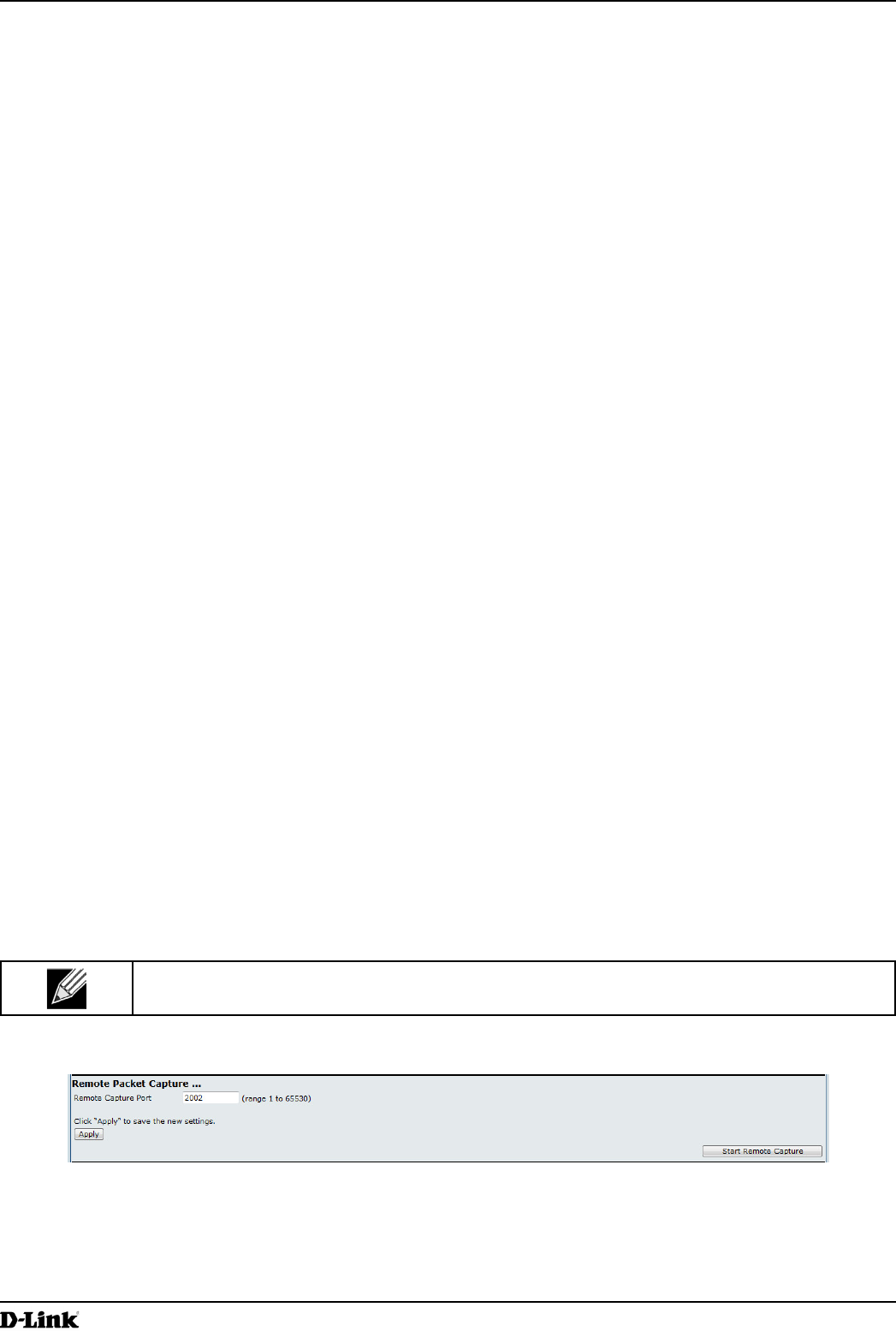
Figure 56 - Remote Packet Capture
The following table describes the elds to congure the packet capture status.


















