Chapter 6: Secure SSH Tunneling and SDT Connector
724-746-5500 | blackbox.com
63
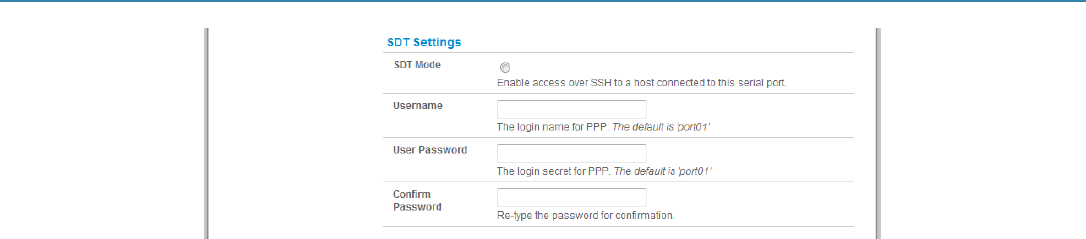
Figure 6-35. SDT settings screen.
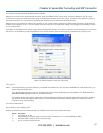
NOTE: When you enable SDT, it will override all other Configuration protocols on that port.
NOTE: If you leave the Username and User Password fields blank, they default to portXX and portXX where XX is the serial port number. The
default username and password for Secure RDP over Port 2 is port02.
Make sure the console server Common Settings (Baud Rate, Flow Control) are the same as those set up on the Windows computer COM port and
click Apply.
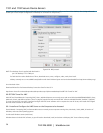
RDP and VNC forwarding over serial ports is enabled on a Port basis. You can add Users who can have access to these ports (or reconfigure User
profiles) by selecting Serial & Network: User & Groups menu tag—as described earlier in Chapter 5, Configuring Serial Ports.
6.10.3 Setup SDT Connector to SSH Port Forward over the Console Server Serial Port
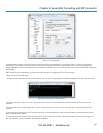
In the SDT Connector software running on your remote computer, specify the gateway IP address of your console server and a username/password
for a user you set up on the console server that has access to the desired port.
Next, add a New SDT Host. In the Host address, put portxx, where xx = the port you are connecting to. Example: for port 1 you would have a Host
Address of: port01. Then select the RDP Service check box.
6.11 SSH Tunneling Using other SSH Clients (for example, PuTTY)
As covered in the previous sections of this chapter, we recommend that you use the SDT Connector client software that is supplied with the console
server. There’s also a wide selection of commercial and free SSH client programs that can provide the secure SSH connections to the console servers
and secure tunnels to connected devices:
PuTTY is a complete (though not very user friendly) freeware implementation of SSH for Win32 and UNIX platforms.
SSHTerm is a useful open source SSH communications package.
SSH Tectia is leading end-to-end commercial communications security solution for the enterprise.
Reflection for Secure IT (formerly F-Secure SSH) is another good commercial SSH-based security solution.
For example, the steps on the next page show how to establish an SSH tunneled connection to a network connected device using the PuTTY client
software.