113
McAfee
®
Host Intrusion Prevention 6.1 Product Guide General Policies
Configuring the Trusted Applications policy
7
Creating trusted applications
In tuning a deployment, creating IPS exception rules is one way to reduce false
positives. This is not always practical when dealing with several thousand clients or
having limited time and resources. A better solution is to create a list of trusted
applications, which are applications known to be safe in a particular environment. For
example, when you run a backup application, many false positive events can be
triggered. To avoid this, make the backup application a trusted application.
To create a trusted application:
1 Do one of the following On the
Trusted Application tab:
Click Create on the toolbar or the shortcut menu. The New Trusted Application dialog
box appears.
Select an application in the list and click Duplicate on the toolbar or the shortcut
menu. A prefilled
Duplicate Trusted Application dialog box appears.
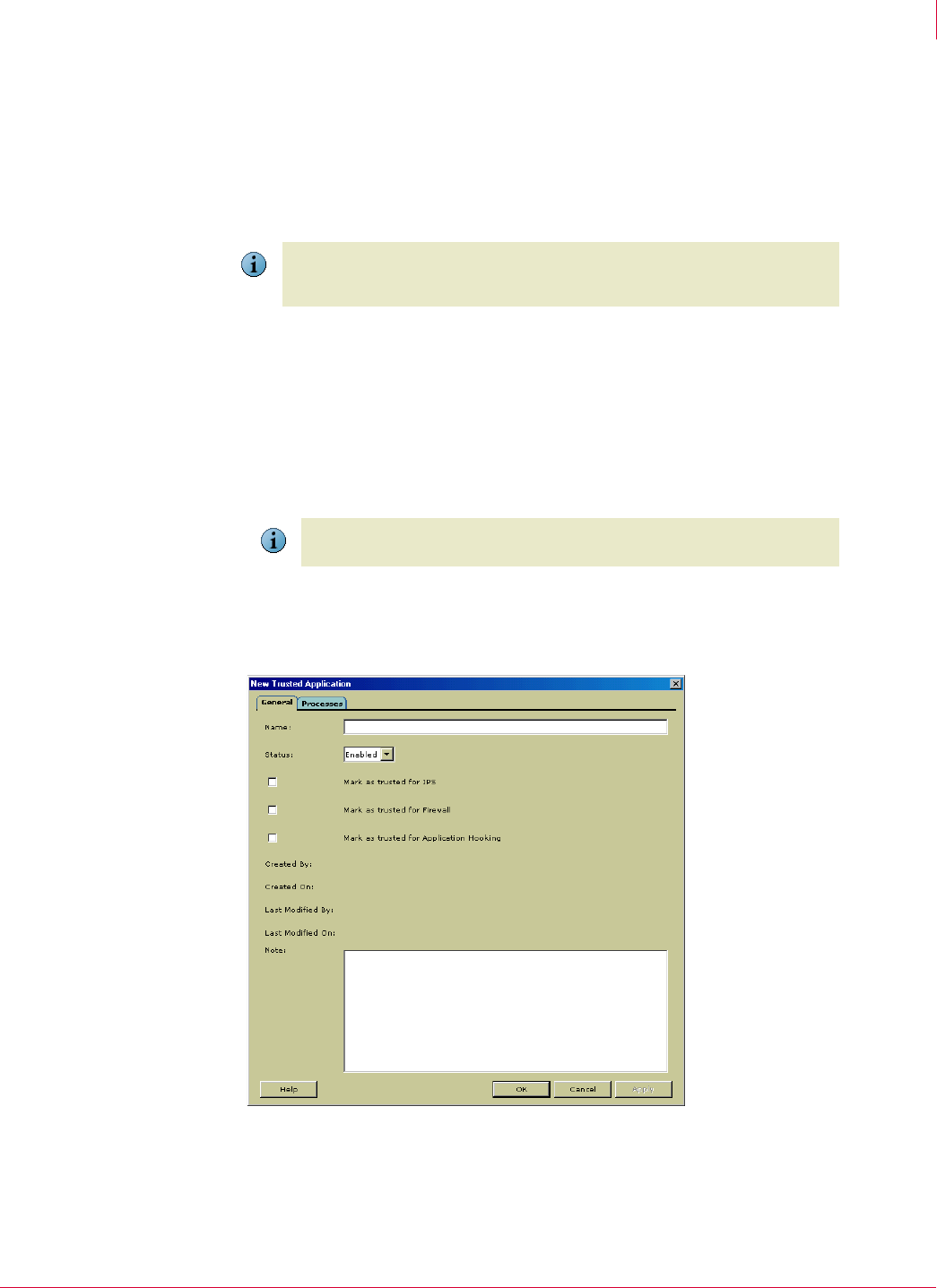
2 On the
General tab, enter the name, status, and whether the application is trusted
for IPS, firewall and application hooking. For details, click
Help.
.
3 On the Processes tab, select the processes to apply the trusted application. For
details, click
Help.
Note
A trusted application is susceptible to common vulnerabilities such as buffer overflow
and illegal use. Therefore, a trusted application is still monitored and can trigger events
to prevent exploits.
Note
You can also create trusted applications based on an event. For details, see Creating
event-based exceptions and trusted applications on page 61
.
Figure 7-8 New Trusted Application dialog box—General tab