54
McAfee
®
Host Intrusion Prevention 6.1 Product Guide IPS Policies
IPS Rules policy details
4
The IPS component maintains an information cache on running processes, which
tracks hooking information. The firewall component determines if a process listens on
a network port, calls an API exported by the IPS component, and passes the
information to the API to be added to the monitored list. When the API is called, the
IPS component locates the corresponding entry in its running processes list. A process
that is not already hooked and is not part of the static block list is then hooked. The
firewall provides the PID (Process ID), which is the key for the cache lookup of a
process.
The API exported by the IPS component also allows the client UI to retrieve the list of
currently hooked processes, which is updated whenever a process is hooked or
unhooked. A hooked process will be unhooked if the console sends an updated
process list that specifies that the already hooked process should no longer be hooked.
When the process hooking list is updated, every process listed in the information cache
of running processes is compared against the updated list. If the list indicates that a
process should be hooked and it’s not already hooked, that process will be hooked. If
the lists indicate that a process should not be hooked and it is already hooked, that
process will be unhooked.
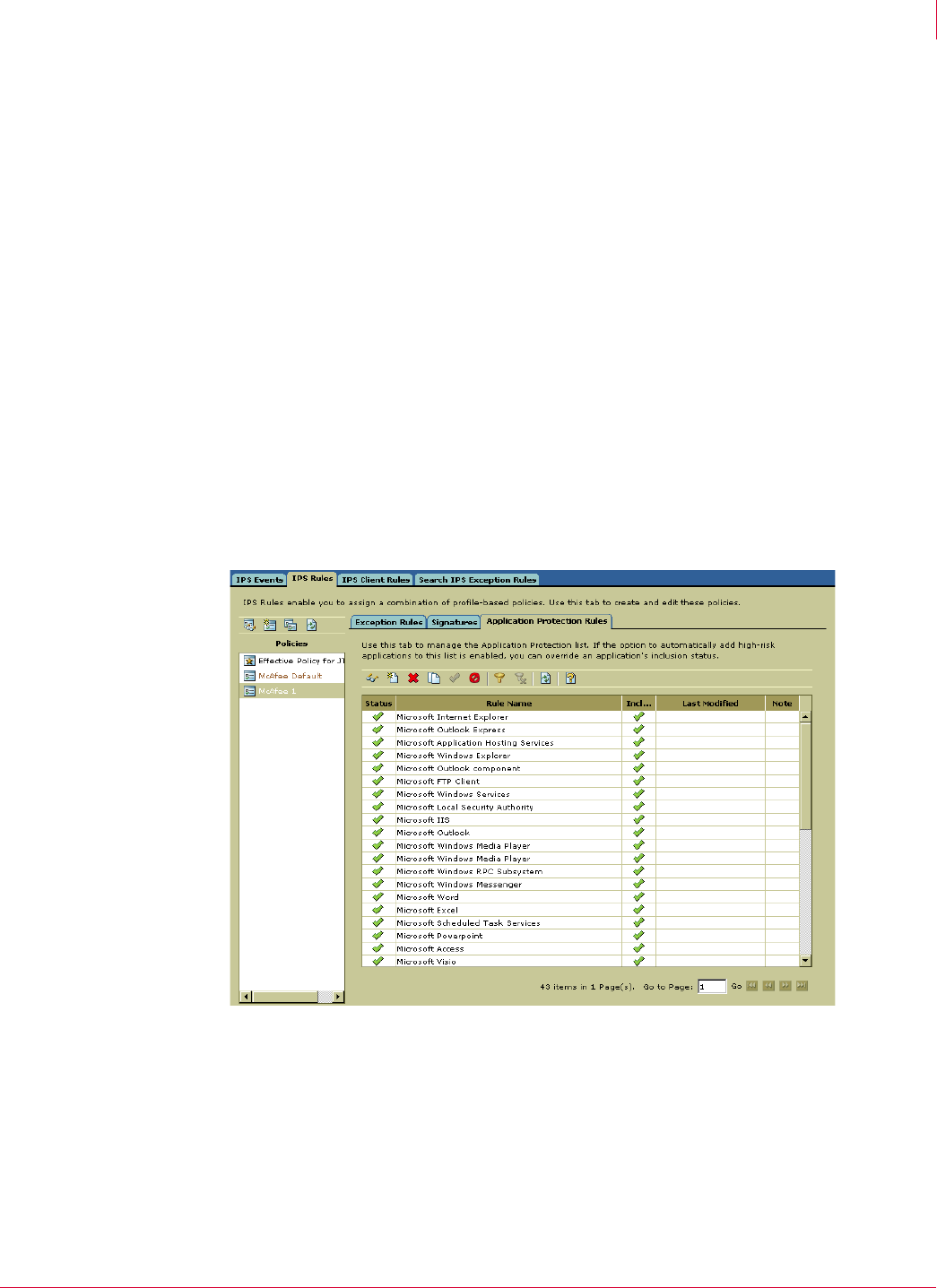
The process hooking lists can be viewed and edited on the
Application Protection Rules
tab. The client user interface, unlike the view on the IPS Rules policy, shows a list of
all hooked application processes.
To create an application protection rule:
1 Do one of the following:
On the Application Protection Rules tab, click Create on the toolbar or the shortcut
menu. The
New Application Protection Rules dialog box appears.
On the Application Protection Rules tab, select an application and click Duplicate on
the toolbar or the shortcut menu. A prefilled Duplicate IPS Application Protection Rules
dialog box appears.
Figure 4-12 IPS Rules—Application Protection Rules