62
McAfee
®
Host Intrusion Prevention 6.1 Product Guide IPS Policies
IPS Events
4
You can create event-based exceptions or trusted applications directly from an event
to prevent the event from reoccurring, or you can create exceptions or trusted
application without reference to any particular event. For the latter, refer to Exception
Rules on page 42 and Creating and applying Trusted Applications policies on page 112.
Creating exceptions and trusted applications allows you to weed out false positive
alerts, and ensures that the notifications you receive are meaningful communications.
Example
For example, during the process of testing clients, you may find clients recognizing the
signature E-mail access. Under certain circumstances, an event triggered by this
signature is cause for alarm. Hackers may install trojan applications that use TCP/IP Port
25 typically reserved for e-mail applications, and this action would be detected by the
TCP/IP Port 25 Activity (SMTP) signature. On the other hand, normal e-mail traffic might
also match this signature. When you see this signature, investigate the process that
initiated the event. If the process is one that is not normally associated with e-mail, like
Notepad.exe, you might reasonably suspect that a trojan was planted. If the process
initiating the event is normally responsible for sending e-mail (Eudora, Netscape,
Outlook) create an exception to that event.
You may also find, for example, that a number of clients are triggering the signature
startup programs, which indicates either the modification or creation of a value under
the registry keys:
HKEY_LOCAL_MACHINE/Software/Microsoft/Windows/CurrentVersion/Run
HKEY_LOCAL_MACHINE/Software/Microsoft/Windows/CurrentVersion/RunOnce
As the values stored under these keys indicate programs that are started when the
computer boots, recognition of this signature may indicate that someone is attempting
to tamper with the system. Or it might indicate something as benign as one of your
employees installing
RealAudio on their computer. The installation of RealAudio adds the
value
RealTray to the Run registry key.
To eliminate the triggering of events every time someone installs authorized software,
you create exceptions to these events. The client will no longer generate events to this
authorized installation.
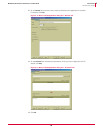
To create an event-based exception:
1 Select an event and click
Create Exception on the shorcut menu or the toolbar.
A prefilled New Exception dialog box appears.
2 Follow the directions for creating an exception in Exception Rules on page 42.
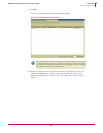
To create an event-based trusted application:
1 Select an event and click
Create Trusted Application on the shorcut menu or the toolbar.
A prefilled
New Trusted Application dialog box appears.
2 Follow the directions for creating a trusted application in Creating and applying
Trusted Applications policies on page 112.