20
McAfee
®
Host Intrusion Prevention 6.1 Installation/Configuration Guide Basic Concepts
Policy management
2
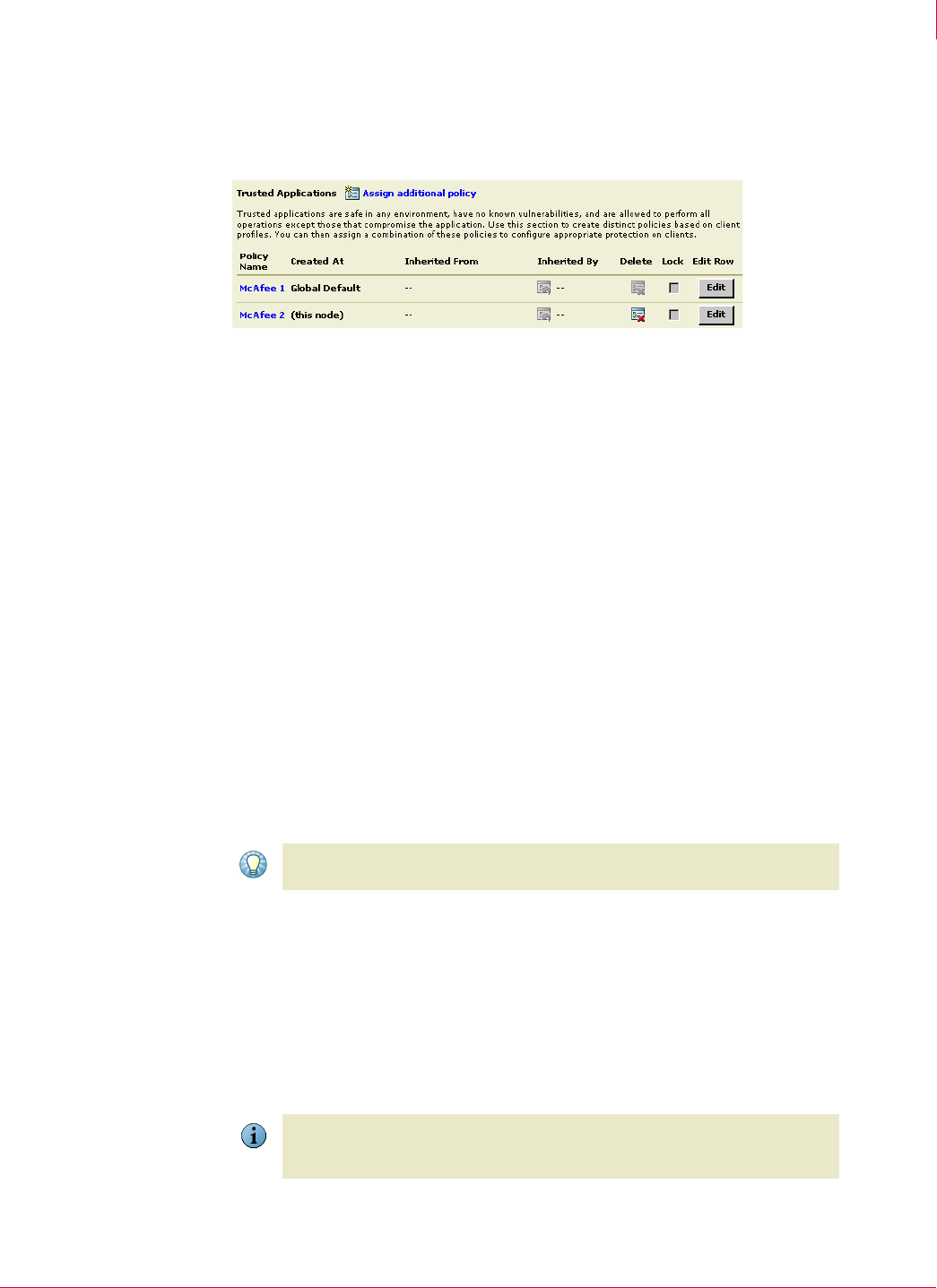
Two Host Intrusion Prevention policy categories, IPS Rules and Trusted Applications,
enable you to assign more than one named policy instances and offer a profile of IPS
and application policies that can be applied
Policy inheritance and assignment
Policies are applied to any console Directory tree node by inheritance or assignment.
Inheritance determines whether the policy settings for any node are taken from its
parent. By default, inheritance is enabled throughout the Directory. You can break
inheritance by direct policy assignment. Host Intrusion Prevention, as managed by
ePolicy Orchestrator, enables you to create policies and assign them without regard to
inheritance. When you break this inheritance by assigning a new policy anywhere in the
Directory, all child nodes inherit the new policy.
Policy ownership
With all policies available, each policy is then required to have an assigned owner. By
default, the owner of a policy is the global or site administrator who created it.
Ownership ensures that no one other than the global administrator or owner of the
named policy can modify it. Any administrator can use any policy that exists in the
catalog, but only the owner or global administrator can modify it.
If you assign a policy that you do not own to nodes of the Directory that you administer,
and the owner of the policy modifies it, all systems to which this policy is assigned
receive these modifications.
Policy assignment locking
A global administrator can lock the assignment of a policy at any location within the
Directory. Policy assignment locking prevents other users from switching the
assignment of one policy for another. It is inherited with the policy.
Policy assignment locking is useful if a global administrator configures and assigns a
certain policy at the top of the Directory to ensure no other users replace it with a
different named policy anywhere in the Directory.
Figure 2-2 A profile of two Trusted Application policy instance
Tip
To use and control a policy owned by a different administrator, duplicate the policy and
then assign the duplicate policy.
Note
Policy locking does not prevent the policy owner from making changes to the named
policy’s settings. Therefore, if you intend to lock a policy assignment, be sure that you
are the owner of the policy.


















