157
McAfee
®
Host Intrusion Prevention 6.1 Product Guide Host Intrusion Prevention Client
Linux client
9
SELinux uses a mandatory access control mechanism implemented in the Linux
kernel with the Linux Security Modules (LSM) framework. This framework checks
for allowed operations after standard Linux discretionary access controls are
checked. Because the Linux client uses LSM, any other application that uses LSM
will not work unless stacking is implemented.
Troubleshooting
After the Linux client is installed and started, it protects its host. However, you may
need to troubleshoot installation or operation issues.
Client installation issues
If a problem was caused while installing or uninstalling the client, there are several
things to investigate. These can include ensuring that all required files were installed in
the correct directory, uninstalling and then reinstalling the client, and checking process
logs.
Verifying installation files
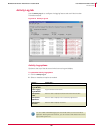
After an installation, check to see that all the files were installed in the appropriate
directory on the client. The
opt/McAfee/hip directory should contain these essential
files and directories:
Installation history is written to /opt/McAfee/etc/hip-install.log. Refer to this file
for any questions about the installation or removal process of the Host Intrusion
Prevention client.
Verifying the client is running
If the client does not appear in the ePO console, for example, check that the client is
running. To do this, run this command:
ps –ef | grep hip
Client operations issues
The client might be installed correctly, but you might encounter problems with the
operation of the client. You can check whether the client is running, and stop and
restart the client.
File Name Description
HipClient
HipClient-bin
Linux client
HipClientPolicy.xml Policy rules
hipts
hipts-bin
Troubleshooting tool
*.so Host Intrusion Prevention and ePO agent shared
object modules
log directory Contains log files: HIPShield.log and HIPClient.log