156
McAfee
®
Host Intrusion Prevention 6.1 Product Guide Host Intrusion Prevention Client
Linux client
9
Linux client
The Host Intrusion Prevention 6.1 Linux client identifies and prevents potentially
harmful attempts to compromise a Linux server’s files and applications. It leverages
the native SELinux protection mechanism, translating IPS policies into SELinux rules
and SELinux events back to IPS events, and provides easy management from the ePO
console.
Policy enforcement with the Linux client
Not all policies that protect a Windows client are available for the Linux client. In brief,
Host Intrusion Prevention protects the host server from harmful attacks but does not
offer network intrusion protection, including buffer overflow. The policies that are valid
are listed here.
Notes about the Linux client
If you have an existing SELinux policy in place or are using default protection
settings, installing a Linux client replaces the policy with a default McAfee Host
Intrusion Prevention policy. Uninstalling the Linux client restores the previous
SELinux policy.
The Linux client requires that SELinux be installed and enabled (set to enforce or
permissive). If it is installed but disabled, enable it, set it to targeted policy, and
restart the computer before installing the Linux client.
Linux controls file attribute changes with a single SELinux permission (file:setattr).
It does not have individual control of chdir or symlink, control of changing directory,
or control of creating a symbolic link.
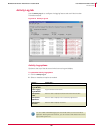
With this policy... These options are available...
HIP 6.1 GENERAL:
Client UI
None except admin or time-based password to allow use
of the troubleshooting tool
.
Trusted Networks None
Trusted Applications
Only Mark as trusted for IPS and New Process Name to add
trusted applications
.
HIP 6.1 IPS:
IPS Options
Enable HIPS
Enable Adaptive Mode
Retain existing Client Rules
IPS Protection All
IPS Rules
Exception Rules
Signatures (default and custom HIPS rules only)
Note: NIPS signatures and
Application Protection Rules
are not available.
IPS Events All
IPS Client Rules All
Search IPS Exception Rules All
HIP 6.1 FIREWALL
None
HIP 6.1 APPLICATION BLOCKING
None